BugBounty story #bugbountytips
A fixed but they didn’t pay the bugbounty story…
Timeline:
- reported 21 Oct 2019
- validated at Critical 23 Oct 2019
- validated as fixed 30 Oct 2019
- Bounty amount stated (IDR 10.000.000 = ~700 USD) 12 Nov 2019
- Information provided for payment 16 Nov 2019
- 13 March 2020 – Never paid – blog post posted
- 19 March 2020 – received bounty of $565.86
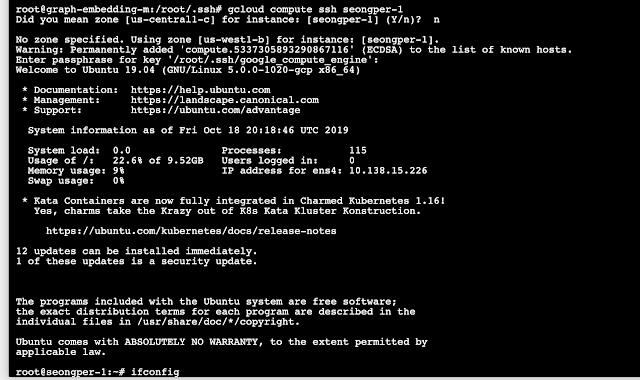
There are lots of applications that are SAAS – Shell as a Service. Jupyter Notebook is one of these with its running code feature as well as its terminal functionality.
While I was trolling shodan looking for vulnerable boxes i came across an open Jupyter notebook belonging to Tokopedia. This wasn’t obvious at first , but it will become clear how I identified this as you check out the screenshots.
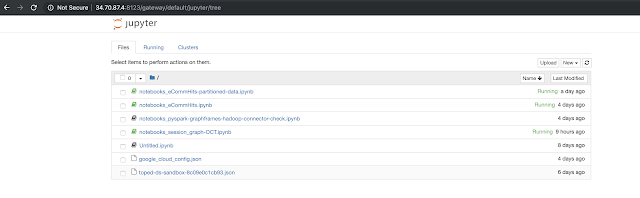 |
| Open Jupyter notebook server |
I did a post on what do do when you find a GCP key in a previous post
This is especially important when people leave their GCP service account keys in folders
 |
| When you leave your service token in the folder for all to find/use |
In this case it was base64 encoded – but easy to fix
 |
| service account token b64 decoded |
It was also in the error output of one of the jupyter notebooks
I had used the terminal to do some basic poking around to find the owner
Once I identified it was owned by someone with a bug bounty program I figured it was ok to prove access and impact.
Per the GCP blog post once you have the service account token you authenticate and interact with services your token has access to
The handy thing about getting a shell on a GCP compute host is that all the GCP utils are installed and “just work” I actually didn’t need to do anything from an external host I was able to start ssh’ing to other hosts from within the jupyter terminal.
Bigquery tables o_0
[+] Bigquery access [+]
bq ls –format=prettyjson –project_id tokopedia-970
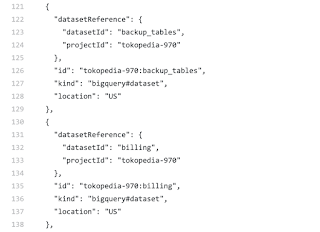 |
| Dat billing table yo |
 |
| I love payments tables |
Along the way I searched who this company was. https://en.wikipedia.org/wiki/Tokopedia
In 2017, Tokopedia received $1.1 billion investment from Chinese e-commerce giant Alibaba.[7] Again in 2018, the company secured $1.1 billion funding round led by Chinese e-commerce giant Alibaba Group Holding and Japan’s SoftBank Group[8] putting its valuation to about $7B.[9]
So being a good person ™ I reported the issue and it was assigned a critical severity. The fixed it super quickly and the team was decently responsive until it was fixed. After that it took 2 weeks to get information on the bounty, I promptly provided payment info, but I was never paid and they have stopped responding to my inquiries.
Solutions:
Run in a limited privilege container (doesn’t protect against cloud metadata attack)
New versions of Juypter notebook allow for password protecting access. Do that instead of open to all