I watched a good DEF CON video on abusing public AWS Snapshots
I, of course, wanted to check this out. There are tens of thousands of public snapshots in the various regions. The talk outlines what you can do with these and Bishop Fox released a tool to do it https://github.com/BishopFox/dufflebag. I wanted to script up a few weirdAAL modules to 1) for an AWS keypair you are testing check and see what snapshots you have available 2) for an AWS accountid list public snapshots. Useful for bug bounty or for monitoring your org for public snapshots. The account you are using will need at least AmazonEC2ReadOnlyAccess privileges.
Screenshot of the 2nd function below
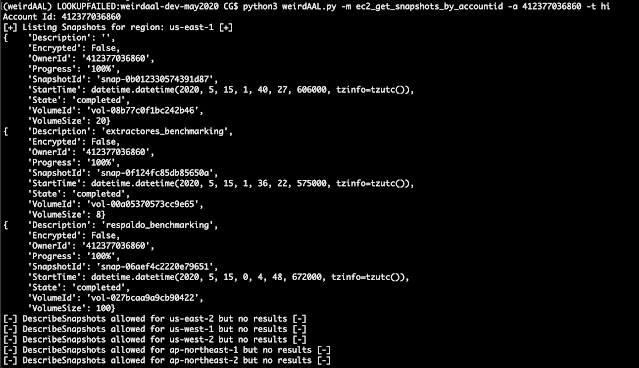 |
| listing snapshots for a random AWS accountid |
You can git clone or git pull to get the updated code from https://github.com/carnal0wnage/weirdAAL
If you just want to do it with the AWS CLI you can use the following shell script:
